While cybersecurity is becoming a more common item on board agendas, The state of pentesting 2023 report from Pentera shows that there is still much to do to prevent cyber attacks. The majority of the respondents to a survey in the report, 88%, said that their organizations have reported attacks in the last two years, even though they were backed up by large investments in defense-in-depth strategies.
The report also found companies in Europe are facing more cyberattacks, and more companies are doing penetration testing (pentesting) to validate their own controls rather than to meet requirements from regulators.
“We’re seeing more organizations increase the cadence of pentesting, but what we really need to achieve is continuous validation across the entire organization,” said Aviv Cohen, CMO of Pentera. “Annual pentesting assessments leave security teams in the dark most of the year regarding their security posture. Security teams need up-to-date information about their exposure using automated solutions for their security validation.”
Increasing budgets
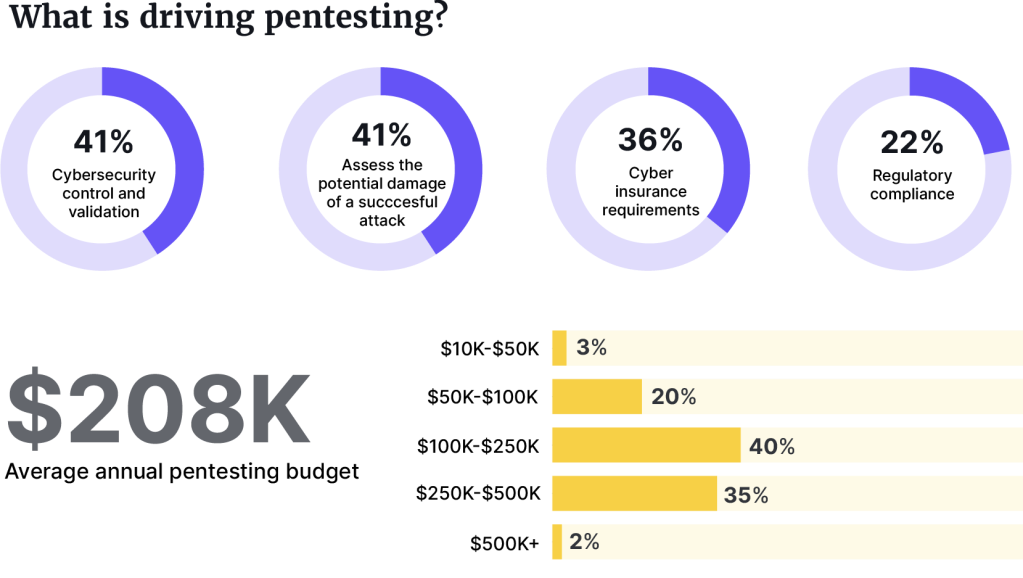
In the report, Pentera surveyed 300 CIOs, CISOs, and security executives from enterprises across Europe and the US. On average, a company is spending $208K on its annual pentesting budget, and has almost 44 security solutions in place. Which indicates a defense-in-depth strategy where multiple security solutions are layered to protect assets. But this has not proved enough to prevent attacks.
The report also shows that pentesting budgets and overall IT security budgets increased significantly for 2023, to meet testing and security requirements, 85% and 92%respectively. For this year, 77% reported a pentesting budget of more than $100,000, a big increase from 2020 when 49% reported a budget of less than $100k.
“We’re seeing more organizations increase the cadence of pentesting, but what we really need to achieve is continuous validation across the entire organization.”
Aviv Cohen, CMO, Pentera
Europe has a slightly higher average budget with $210,885, compared to the US average of $205,947. Companies with under 5,000 employees had an average $196,430 budget, compared to $228,777 for companies with more than 5,000 employees. Neither region nor company size appears to significantly affect the size of pentesting budgets.
Regulatory compliance
Most security leaders had been conducting pentesting as a step in required regulatory compliance work. Now, more are driven by the need to validate their own systems, as well as to assess the potential damage of a successful attack.
CISOs are also saying that they are using the pentesting reports as “a more concrete way to communicate risk to the board of directors or to other executives within the organization who may not be as security-savvy”. They are also sharing their results with customers and regulators, in order to provide assurances to stakeholders that their security is robust.
Another change uncovered in the report is that 36% said cyber insurance was a reason to adopt pentesting. Only 2% cited this as a reason in 2020.
On how often the pentests were performed, the respondents said:
- Daily – 8%
- Monthly – 11%
- Quarterly – 32%
- Biannually – 21%
- Annually – 29%
The majority, 82%, reported that they are pentesting as part of their overall security strategy. Some 42% said they were using an external party for the testing, while 39% are testing in-house for more independence, efficiency and a greater validation frequency. However, the report shows more room for growth as only 15% claim to be on the advanced end of the security validation maturity scale.
Red teams
The number of in-house red-teams has also grown – red teams play the role of an adversary to provide security feedback from an antagonist’s perspective. Now, 67% of respondents said they have an in-house team, 4% said they did not, and 29% are planning to have one in place this year. However, almost all say that they are expecting to have an in-house red team by the end of 2023 (96%).
On the question of why the companies don’t conduct manual pentesting more often and what the barriers are, most replied that they were afraid of risk to business continuity (45%), and the availability of pentesters (41%). A third, 33%, said it had to do with budget. The figure was higher in the US (41%) compared to ‘only’ 25% in Europe.
About a fifth, 21%, said that regulatory mandates don’t require more testing, and the same percentage said that they don’t have the internal resources to remediate. Finally, 4% said that they don’t need more testing.