It’s always a great discussion when Ian Amit and Darren Hayes are a part of it. Amit is a well-known computer security researcher, hacker and executive, and the CEO and co-founder of Gomboc.ai, a company helping to detect and solve cloud infrastructure security threats. Darren Hayes is a professor at Pace University and forensic examiner who also is the CEO and founder of CodeDetectives LLC, providing forensics and incident response technical expertise to businesses worldwide.
We sat down 2023 style – over Zoom – to discuss cyber resiliency, artificial intelligence, data exfiltration, ransomware, incident response and other things that keep chief information security officers (and the rest of us) up at night.
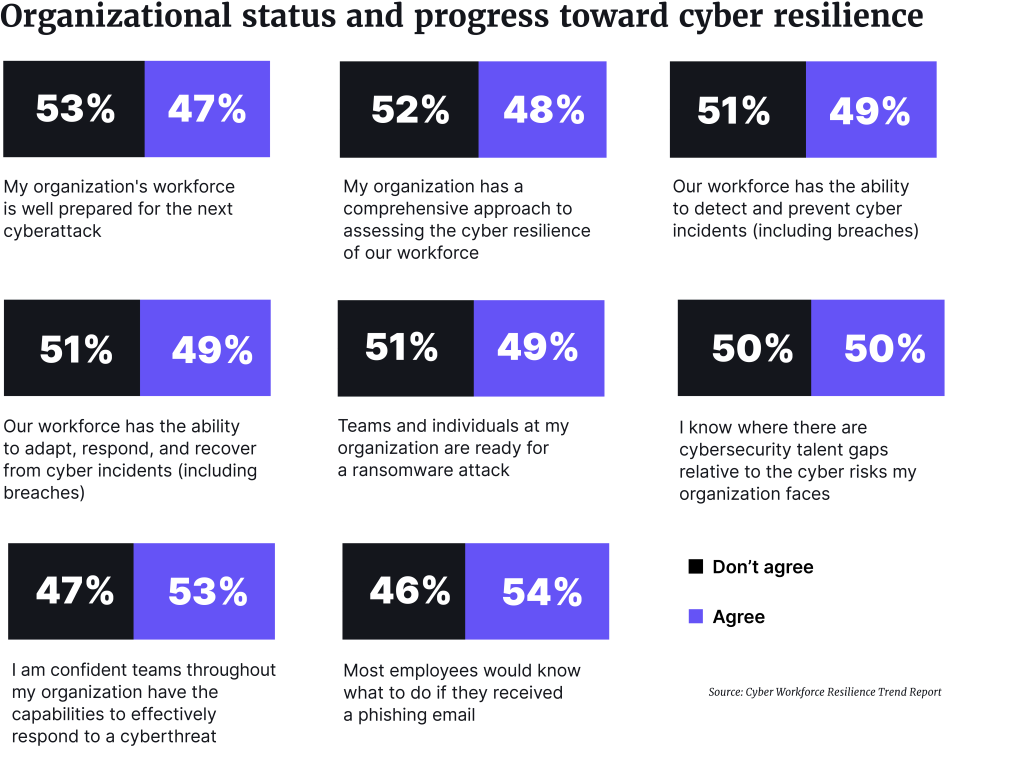
Skills gap
We asked them first about a survey that was carried out by Osterman Research for Immersive Labs in November 2022 and the report that was generated from its results. The 570 respondents were senior risk and security professionals at organizations with more than 1,000 employees in the UK, US and Germany.
The report showed that most respondents were more focused on upskilling existing team members rather than hiring new cybersecurity professionals. Is this surprising to them?
“No,” was the answer. A couple of things are likely happening, they said. There is a higher bar to start with these days, so it’s harder to hire for these roles. And it does not help that a good number of them are creating their own companies now too, given the demand for their expertise.
“There is a skills gap that can be filled with automation,” Amit said. “You can automate a lot of manual work so people with certain skills sets can optimize their focus and workloads. Using the right technology and niche tools to create more efficiency and to use these peoples’ skills in a more targeted way makes great sense.”
Artificial intelligence
That prompted thoughts of generative AI – how it’s being touted for its time-saving resourcefulness in workplaces, but also how it’s also being questioned for various ethical and appropriateness reasons.
Amit says the idea that it’s going to steal away a lot of people’s jobs is just silly. We will have some job losses, but some new ones will be created too as those are new businesses and business lines themselves, and the tools will make us more efficient.
“Automating tasks is not going to go away, but, yes, some applications for it will be horrible and require some regulation, but any over-correction (like Italy’s initial outright ban of generative AI) is foolish. Since it has the capacity to advance society and the economy, just put some regulatory fencing around it that still enables it to accomplish those goals,” he said.
Hayes agreed. “People are overwhelmed in their jobs when it comes to managing data; they need these tech tools. I just worry they won’t have the time to take the training that is required to use them correctly,” he said.
Hayes also worries that many forensic imaging tools were developed for law enforcement to use, and now incident responders in companies are using these same tools for a different purpose, which can be problematic. “It’s one challenge facing crisis management teams now – using tools designed for law enforcement that primarily focus on user-created evidence rather than incident response, which focuses on operating system changes.”
We put it to the pair that organizations always needed the human judgment that comes with solving problems – that the technology culls the information and streamlines it, and people add the value of context.
Amit agreed. “People add context, exactly. But, if you want the tool to come up with solutions, it will, as it sees it as a mathematical challenge. They are programmed to come up with a solution when you ask them for one – and that’s where we need to be careful.”,
Data exfiltration
Switching to a new topic, we asked them about data exfiltration, as we wanted to know how an organization can know its data has been taken. It’s even harder than many thought.
Hayes said the FBI will typically contact you if it is a state-sponsored attack. But the first thing you need to realize, no matter what type of attack it is, is that it’s probably been stolen for a while and over the course of some time. And it will be hard to detect exactly how much is gone.
“I would not categorically exclude paying a ransom from an incident response plan.”
Ian Amit, CEO and co-founder of Gomboc.ai
Amit said it’s not overly helpful to look at traffic patterns in your data, as the savvy hackers often cater their work around your traffic flow, since they have been studying you. “It’s often law enforcement or the bad guys themselves telling you that data has been compromised,” he said.
If it shows up on some data server somewhere and is being traded on, or something akin to that, threat intelligence services can help find them in the dark web and on chat forums, he said, although he can’t attest to their efficacy.
Amit stresses that he means companies you contact for services – not ones that reach out to you to help you. Those are enterprises you should avoid!
Ransomware
Thinking about data being taken made us think of the increasingly common, reputation-damaging threat of a ransomware attack.
Studies show that ransomware cost the world $20bn in 2021 and is expected to rise to $265bn by 2031. Out of all ransomware victims, 32% pay the ransom, but they only get 65% of their data back.
A number of US states have regulatory requirements around how quickly you must report having paid a ransom, and some states prohibit ransomware payments by all state and local government agencies. The FBI has a strict advisory against paying one, saying that it considers the payments an action in furtherance of state-sponsored terrorism or assisting a sanctioned entity or jurisdiction.
So what are the pair’s thoughts about businesses paying a ransom?

Photo: Private
“At the end of the day, it’s a business decision to be decided on a case-by-case basis,” Amit said. “It should be an option. Some businesses might use it as a last resort, but some might think it makes 100% sense to get that data back earlier. It should be a tool and a business decision we leave to the business,” he said.
Hayes agreed that it completely depends on the situation, and if your insurance policy will help pay some of it. “Plus, it might be more clear-cut if we are talking about healthcare where people’s lives depend on the data that was taken,” he noted.
“Now as I say that, I’m setting aside legal obligations, OFAC obligations, and ethical concerns, of course – and those need to be considered. But I would not categorically exclude paying a ransom from an incident response plan”, Amit said.
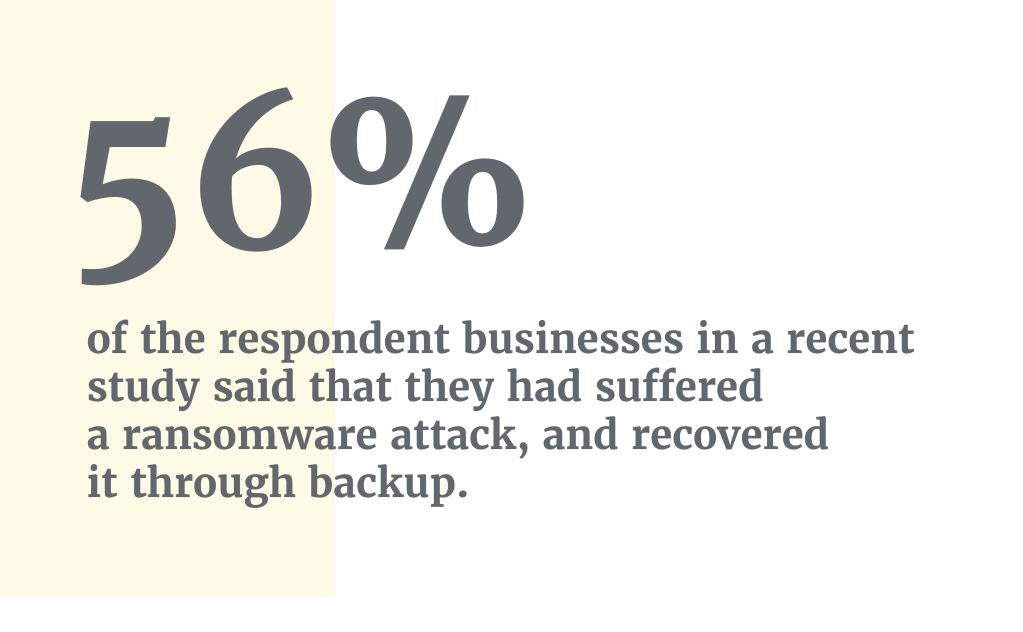
Your backups are incredibly important, Hayes added. He said a recent study showed that only 56% of respondent businesses that had suffered a ransomware attack, and had their data encrypted by attackers, managed to recover it through backups.
That figure shows just how important backup can be in tackling ransomware, but it also highlights that there are many organizations missing a critical component in their defense posture.
Hayes says you need to consider what data was encrypted. Businesses should remember that not everything needs to be on a network computer, he said. Some things could be put on an airgap computer, for instance.
Backups
But the bad guys often sell this data on the dark web right away – so how do backups really help?
Hayes pointed out that, even worse, even if you pay the ransom, the hackers sometimes still sell the data or some of it. So, true, backups are not a panacea.
Ian said it all boils down to a cost analysis. If my backup rots, it might take me a week or month to get back in business – and paying the ransom might get me back to business in a day. So that $250,000 ransom payment might make sense.
“TikTok is a truly bad app – I would fully prohibit it.”
Darren Hayes, CEO and founder of CodeDetectives LLC
And even if they still them sell some of the data on the dark web, maybe that’s the chance you take, and maybe that leads to some heartache, but over 6-12 months you are likely to be back in action,” he said.

“It cannot be: ‘though shall not pay a ransom.’ It has to be an analysis of the costs to the business, based on the options presented; how can we minimize the impact to the business; and what is the quickest way to get back to business?” Amit said.
They both emphasized that paying the ransom is not the best first option. Spending your money on good backups should be a primary concern, however. Along those lines, do some painstaking research on your cloud provider offerings, they advised.
The cheaper ones might require you to pay a lot of money on the download part when it’s time to retrieve data, as they are storing it in a different format. You only saved money on the initial loading of the data; converting it from long-term to short-term storage can cost a great deal of money, which in a ransomware scenario, can make you feel “ransomed” twice.
There are like 300 different types of cloud services. Really examine the capabilities of each one, Amit cautioned.
“But if you’re stuck in the position when backups have not been as strong as they could have been, I might need that ransom payment option,” Amit said.
Incident response
We listed the members of a possible incident response team, and Amit made sure to note that he wants the CFO not just there, but in an active role.
“It is really good to have the finance folks there,” he said. “The CFO should lead the discussion of whether to pay a ransom, for example, after consulting with others on the team about legal, regulatory and insurance-based considerations.”
Hayes said outside experts such as cyber legal professionals certainly have a role to play. They can analyze the legal risks the business faces. Outside incident responders as consultants are helpful, he said, but those legal minds are truly needed.
Amit said the business needs to do the math. Sometimes the outside experts can help accelerate the incident response processes to help fix things sooner – so you should do the math of paying them, versus the time they might help you save.
So what often goes awry in an incident response?
Amit said one big problem is an incident response plan that exists on paper only. “Exercises need to happen, and not just tabletop ones (which should happen too, so top executives can see the plans), but you need to make sure people don’t just improvise. Do a simulated attack – red team style – one almost no one knows is a drill. I mean, do it like people will think they’re going to lose their jobs – they are actually sweating bullets,” Amit said.
“Late on a summer Friday?” we suggested. “Exactly,” Amit said. “Right before a holiday. Actually, call all the people you’d need to pull in – the outside consultants, everyone and everywhere,” he said.
“Honestly, one surprising thing is that some of the people who are so helpful on the incident response team do not have technical skills at all – because they think about the impact on people, and they think about the impact on job functions and morale, all of which are important,” Hayes observed.
Amit agreed. The incident response leader should not be too technical, he said. “You need to coordinate the response and not just focus on the bits of data. You have to use what’s at your disposal. Tap the folks even in HR to help you with the people elements.”
Amit said he loved the chief information security officer role when an incident happened – he liked putting his training into play and the stress of it was something that fueled him.
Use of personal apps
He also thought we should embrace the use of personal devices; that is, as long as the folks like him in the IT world build the technology to help us use those devices more safely.
“It’s my job to let you do it safely with the right infrastructure and tools around it. As we all know, there is technology that helps you use these devices and apps like WhatsApp more safely, so let’s not stand in the way of better and more efficient business being done in a timely way with them,” Ian said.
“Go wild and be aggressive and be innovative – it’s my job to let you do that,” Amit said.
“The FBI might have useful, historical insights into the group targeting you, so definitely talk to them.”
Darren Hayes
Hayes was a bit more apprehensive. “I might be a little more conservative than that,” he said. “TikTok is a truly bad app – I would fully prohibit it. Organizations need to look at each of the applications and design policies, procedures and monitoring technology around the risks they each present, knowing that people are going to use these things anyway,” he said.
Amit agreed about TikTok, saying he doubts there’s a good business rationale for using it anyway.
The problem with training, Hayes said, is that so much of it is done over email. “’Here is your legally required training!’” That sort of approach is not helpful. But if it’s tailored to the different types of data and data usage that departments are facing, that is more effective. Then they can spot the data they are responsible for and what threats they specifically might be able to intercept.
“Each business has its own risk profile and tolerance and a different understanding of the value of its data; tailor training around those things,” Amit said.
Best practices
We suggested a list of best practice pointers.
Businesses should have:
- tested and reliable online backups;
- local backups of different devices (cloud);
- a zero-trust approach;
- multi-factor authentication (MFA) for all logins;
- no more data stored than needed;
- technology investments at all levels to monitor login attempts, permissions, onboarding, behaviorally analysis of activity;
- battle drills conducted regularly;
- knowledge of where critical data resides;
- checks on the adequacy of cyber insurance;
- made sure the latest security patches are up-to-date; and
- regular security assessments, penetration testing and vulnerability scans.
Hayes said checking on access control and on outdated privileges is a big one – many companies don’t audit those permissions enough.
“Do the penetration testing at a cadence that matches your security posture due to your existing and any new business lines and new applications – set the cadence according to that timescale, and don’t just set it quarterly or annually.”
Ian Amit
Do these people really need access to all of this versus just segments of it – and does this external expert who was in your organization last year still need access?
Amit hones in on zero trust, saying you should have it.
“Zero trust is not just about not assuming that you’re not trusting anything, but it’s also examining permission sets and asking why they exist. What was the last use of it – and do we need to disable it temporarily at least? Maybe keep an account inactive for when the consultant comes back – but not active!”
Hayes agreed and said people should pick up the phone and verify things with others. It can be simple to verify identities. Fraudsters know all the ways to contact you – not just one-off texts now. And with AI, you need just two seconds of someone’s voice. So, it’s best to authenticate everyone,” he said.
MFA should be integrated into all the password tools you use as a standard ingredient. You don’t even have to remember passwords any more – you get a text to verify or click a checkmark or respond via simple facial recognition. There’s no excuse any longer, Amit said.
We asked how often battle drill should be performed.
“Do the penetration testing at a cadence that matches your security posture due to your existing and any new business lines and new applications. Set the cadence according to that timescale, and don’t just set it quarterly or annually,” Amit said.
For bigger exercises, like red team ones, do those at least annually – at a time that is bad for everyone! Again, these cyber incidents generally start on Friday afternoons, and often near holidays, so flex that muscle and do it when it is the least convenient time. Maybe some executives need only to be briefed about them, but many others need to be actually involved in them, he said.
Hayes said companies must also be careful to monitor geopolitical events. Communicate with the FBI about them and consider how and whether they might affect your business.
Working with the FBI
We asked about working with the FBI, Secret Service, and Immigration and Customs Enforcement, among other federal agencies, for assistance during an actual crisis. Amit advised knowing the motivations of everyone with whom you consult.
“The FBI looks at the big picture and has a different perspective and objective than you. They might find it advantageous to allow the attacker to sit inside your organization and monitor its progress and get a better understanding of the attacker. Certainly, you should communicate with them – but your incentives might not be aligned. It’s not a criticism of them – use their knowledge – but focus on your business’s needs. Run your own numbers for the decision to pay a ransom, for example,” he said.
“The FBI might have useful, historical insights into the group targeting you, so definitely talk to them”, Hayes said.