Ransomware and other cybercrimes have been on the rise for the better part of the last three decades. From the professionals behind the $4bn WannaCry ransomware attacks in 2017 to the 15 year old super-hacker “Mafiaboy”, who used DDoS to cripple Yahoo, Dell, eBay, CNN, and Amazon’s websites in 2000, almost anyone with a computer and internet access can now carry out large-scale hacks.
To improve their security infrastructure, corporates have turned to wargaming, a strategy borrowed from the military, conducting red team/blue team exercises to test the strength of their defenses.
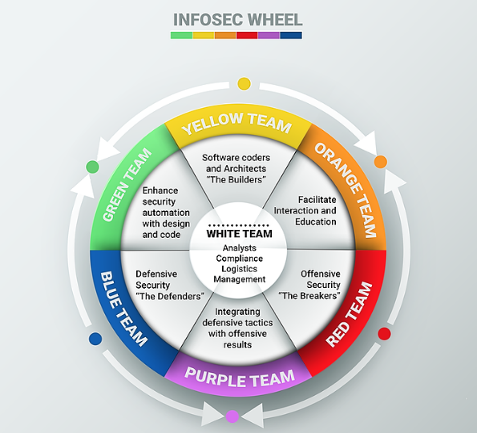
Red and blue teams are the standard security teams tasked with enhancing organizations’ cybersecurity through continuous testing that identifies vulnerabilities and ways to address them. They face off in these exercises just as armed forces do in combat drills: red on the offense and blue on the defense.
Red teams are security experts tasked with testing the effectiveness of firms’ cybersecurity systems by imitating likely attackers’ tools and methods. Known as ‘white hats’ for their ethical hacking, they utilize real adversaries’ tactics, techniques, and procedures to identify vulnerabilities in systems, applications, infrastructure, and human behavior.
Shortcomings of the red-blue divide
Facing them are the blue teams, the internal security experts who defend organization from real adversaries and red team engagements. Based in the cybersecurity operations center (CSOC), these are the analysts and engineers responsible for stopping attacks and breaches through threat prevention, detection, and response.
The goal for red teams is to expose a security flaw. For blues, the goal is to bolster detection and response systems. This testing improves security and stops data breaches, as it shores up an organization’s defenses by continually revealing its weaknesses and preparing it for real attacks.
“A red team looks at your entire castle; it basically says can I undermine you? Can I feed the dragon in the moat and lure it away?,” says Robert Hawk, senior security administrator at Global Relay. “The dragon and the moat are kind of like the intrusion detection system or the advanced response. Then you have your castle gate, that’s your firewall. You have your archers on the castle, that’s again a type of monitoring and response system. So we’re trying to figure out which of these defensive postures are working. Are all these things actually layered properly in the defense and depth posture?”
Red and blue teams share the ultimate purpose of improving organizations’ security, and they do. But the reality is that their competition causes friction, and the two don’t always work in harmony.
They are usually separated physically and their actions disconnected. There is often no feedback channel and as a result, teamwork suffers. There are gaps in methodology, tools, and timelines arising from divisive internal politics, slow feedback loops, an adversarial culture, independent design, and anything else enforcing the harmful belief that they are separate efforts.
A lack of cooperation is common in corporates with unbridled, overly competitive red and blue teams. If security processes are poorly defined and personal interests at stake, team conflicts will arise that necessitate a facilitator.
Bringing out the best of red and blue
This is where purple teams come in. They serve as a bridge between red and blue, fostering communication and cohesion. Purple teams enhance an organization’s cybersecurity capabilities by promoting collaboration and facilitating more effective testing.
“Red teams and blue teams have their own advantages and limitations. What purple teams do is create a feedback loop between the two and fill the gap. As a result, attacks are mitigated proactively in the early phases of the software development lifecycle. [Purple teaming] ensures the design as well as the code can protect the application against not only common attack but also advanced exploitation techniques,” explains Trupti Shiralkar, security and privacy leader at Confidential.
Purple teams are a relatively new concept, and there is no one-size-fits-all definition. Some are combined internal teams, while others are separate external teams or a combination of non-tangible functions. They usually combine a mix of red and blue team skills.
Most purple teams are established as an internal resource comprising some of a firm’s existing red and blue team members. This approach capitalizes on upskilling current team members to boost a firm’s analytical capabilities. By redeploying people who are already familiar with the system in this way, firms secure a superior mix of red and blue talent, boost operations speed, and reduce cost, which helps them to develop a multi-faceted security posture.
“By focusing on developing teamwork rather than adding another team, they save resources, polish their procedures, and enhance cross-team functionality, which advances collaborative security.”
Other firms hire entirely separate, external purple teams of cybersecurity experts with both red and blue skills. This approach solves the problem of the finite pool of analytics talent at one’s own firm. By recruiting specialists for this specific task, firms can acquire top-quality talent without losing time to training, build strategic partnerships, and fill missing capabilities on-demand, enabling them to introduce comprehensive security initiatives without added stress.
Some firms don’t create a third team; instead, they view purple teams as an opportunity to improve cooperation between their red and blue teams. By focusing on developing teamwork rather than adding another team, they save resources, polish their procedures, and enhance cross-team functionality, which advances collaborative security.
The best do some of each, co-creating internally to develop purple talent and externally to expand their abilities, all while promoting collaboration across the security function to expedite the testing process.
How do purple teams operate?
Regardless of their form, purple teams improve cybersecurity by maximizing the effectiveness of red and blue teams through collaborative simulations of likely adversaries’ attacks.
Red-blue exercises consist of campaign testing, where red teams mimic a likely threat’s tactics, techniques, and procedures (TTPs) for extended periods through a series of engagements with realistically tailored goals while blue teams try to stop them. Red’s methods include social engineering, vulnerability assessments, credential theft, penetration testing, and phishing. Blue defends with risk intelligence analysis, security monitoring, software maintenance, reverse engineering of attacks, vulnerability scans, and much more.
Purple teaming enhances the testing process, and therefore a firm’s defenses, by filling the security gaps caused by red and blue teams’ lack of cooperation. It does this by getting intelligence flowing between blue and red team members, refining test procedures, and promoting teamwork. Red learns how blue counters offensives, and blue learns how red evades defenses.
This knowledge sharing, driven by purple teams, is what advances security – it’s all about collaboration.
Purple Team Exercise Frameworks (PTEFs) are the blueprint for this red-blue-purple testing. These are full-knowledge engagements – the attack is explained to the blue team as it occurs, while they work through each TTP and defense protocol jointly to bolster security in real time. Usually human versus human, “purple hacking” can be autonomous; next-gen security platforms simulate attacks and provide mitigation tips.
Purple team activities, both during attacks and around them, include threat intelligence, recognition and analytics, adversary emulation, red and blue training, and evaluation and engineering.
While every organization has its own PTEF, they all follow the same general process. First, planning has the red and blue teams collaborate on how the exercise should look, establishing clear and feasible objectives and activities. Assessment sees the plan’s continuous refinement to ensure the red team meets tactical milestones and the blue team’s defenses meet expectations. Collaboration is required for the blue team to accurately determine if it is detecting the correct activity and for the red team to know which areas to target. In cases of successful attack, remediation allows them to eliminate vulnerabilities jointly. These culminate in iterative reports informed by both that provide a complete analysis of the firm’s security.
The most widely used Purple Team Exercise Framework (PTEF) is MITRE ATT&CK, of the ATT&CK knowledge base, which develops threat models for the private sector, government, and security sectors. Other popular PTEFs are Lockheed Martin’s Cyber Kill Chain, the EU Central Bank Framework for Threat Intelligence-based Ethical Red Teaming, the Hong Kong Monetary Authority’s Cyber Resilience Assessment Framework, and Global Financial Markets Association’s Framework for the Regulatory Use of Penetration Testing in the Financial Services Industry.
Purple team activities, both during attacks and around them, include threat intelligence, recognition and analytics, adversary emulation, red and blue training, and evaluation and engineering. It’s used in healthcare organizations to strengthen security controls and assess program efficacy, in corporations to identify weaknesses in their human operations capacity, and in multinational businesses to identify the risks associated with foreign regulatory policies.
“When red and blue teams work together as a purple team, they can perform assessments in a fashion similar to unit tests against frameworks, like MITRE ATT&CK, and use those insights on attacker behavior to identify gaps in the network and build better defenses around critical assets. Adopting the attackers’ techniques and working with the system to build more comprehensive assessments, you have advantages your attacker does not,” says Hickey.
Purple teams, greener (cybersecurity) pastures
The security benefits of purple teaming are much more than simply improved cooperation, enhanced red and blue team capabilities, and cybersecurity assurance.
Purple teaming helps companies develop a healthier cybersecurity culture, with robust defenses and a symbiotic approach, and facilitate constant communication between offense and defense. The most deliberate gain is that purple teaming erases the adversarial red-blue dynamic, raising exercise efficacy and, more importantly, solidifying a synergistic security posture.
This collective security aligns the interests of red with blue; purple bridges the gap, prioritizing the firm’s defense in a beneficial feedback loop, allowing unbiased detection and response controls. The success of such controls helps to rationalize security investments, building support for CSOC, and optimizing defenses. They identify unneeded defenses more effectively, saving time and cutting costs without extra risk.
Vulnerability detection improves as blue teams receive the knowledge they need to collaborate with reds on better incident identification. Strong feedback loops allow continuous information to be shared continuously; this makes leveraging threat intelligence easier, enabling security to rank and thwart threats. This collective approach provides a more accurate measure of controls covering the entire attack chain, bringing precise security insights.
Purple teaming increases CSOC knowledge and capacity as all teams observe simulations, prepping for real attacks in the process. This helps firms to adapt to the rapidly changing cybersecurity landscape.
“Do not wait for a breach to take place to appreciate the importance of security. In the world of security, anything can be a weakest link including system, network, application, or humans.”
Trupti Shiralkar, security and privacy leader, Confidential
“Many attackers are opportunistic and will frequently move onto an easier target when they encounter resistance, and strong resistance comes from purple teams. Purple teams are used to provide a level of assurance that what you’ve built is resilient enough to withstand modern network threats by increasing the visibility and insights shared among typically siloed teams,” says Hickey about how purple teams provide security assurance.
Purple teams produce a healthier cybersecurity posture for their organization. They build on the merged capabilities of red and blue teams collaboratively to establish better infrastructure and policy, ultimately creating a stronger, quicker, and more precise response to every threat thrown their way – while averting the inner turmoil that doomed them before. This forces a change in perspective.
“My advice to organizations is do not wait for a breach to take place to appreciate the importance of security. In the world of security, anything can be a weakest link including system, network, application, or humans,” Shiralkar says. “One or more AppSec engineers are not sufficient to protect all of the products and newly developed features. Scale AppSec by training your developers. Empower your workforce with knowledge about security and attacks. The more trained developers that you have, the fewer vulnerabilities that will occur and the less the cost of remediation.”
In the future, the cybersecurity function will be more proactive, more technologically innovative, and more refined. The emphasis has shifted from independent teams reacting to attack to consolidated units proactively defending them – we expect this trend to continue.













