Cybersecurity attack attempts across the world increased 104% last year, the report The Anatomy of Cybersecurity: A Dissection of 2023’s Attack Landscape shows. Utilities (over 200%) and manufacturing (165%) were two of the industries at most risk with the largest increases.
The report, which comes from the asset intelligence cybersecurity company Armis, warned that “all industries are vulnerable. All are at risk”. It also revealed more than half (55%) of IT professionals agree with the statement “My organization has stalled or stopped digital transformation projects due to the threat of cyberwarfare”.
And almost a quarter (24%) of all global organizations feel underprepared to tackle cyber threats.
“Cyberwarfare grew more widespread in 2023. Top industries exposed to attack from Chinese and Russian actors were those within manufacturing, educational services and public administration,” said Curtis Simpson, CICO at Armis.
Geopolitical tensions
During 2023, Armis saw an increase in nation-state cyberattacks, linked to cyber war and tensions with China, Russia, Ukraine and Israel. Over 120 countries were targeted during the year, with 40% targeting government or private-sector entities involved in critical national infrastructure.
“In manufacturing, .cn and .ru domains contributed to an average of 30% of monthly attack attempts, while attacks from these domains on educational services have risen to about 10% of total attacks,” Simpson said.
“All industries are vulnerable. All are at risk.”
Armis
The fear of China possibly infiltrating critical infrastructure also ”grew exponentially”, which led to a ban on TikTok in the US. By June 2023, more than half of the US states had either totally or partially banned the social media app on state-issued government devices.
By the end of the year, countries such as India and Nepal had banned TikTok completely, and lawmakers in the US, Europe and Canada had made further progress to restrict access to it. In Nepal, the ban rose from more than 1,600 TikTok-related cybercrime cases over four years – all coming from China.
But even with rising and more malicious attacks, one third of organizations globally (33%) are still said not to be taking threats of cyberwarfare seriously, and are either indifferent or unconcerned about the impact of risks.
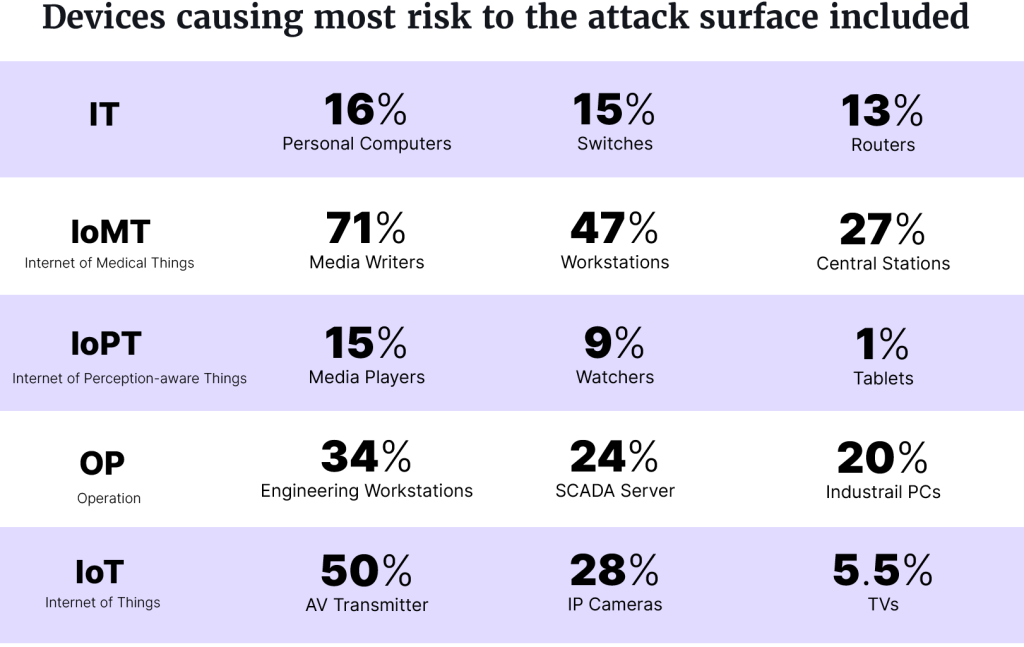
“Gaining the intelligence from the data shared above is one thing, but in order for these learnings to have a real impact, it’s crucial that security teams proactively leverage them to improve their defenses,” Simpson continued. “These findings should be thought of as a blueprint to help teams focus limited resources on efforts with the greatest impact.”
Another of Armis’s findings was the vulnerability trend in older operations systems. Devices that were using Windows Server OS versions from 2012 and older were 77% more likely to be exposed to attack attempts compared to newer versions.
72% US increase in compromises
The increase in attacks during last year was also noted in the 2023 Annual Data Breach Report by the Identity Theft Resource Center (ITRC). A total of 3,205 compromises, of which 2,365 were cyberattacks, were identified in the US – an increased of 78% on the 1,801 in 2022. Over 353 million victims are estimated to have been affected.
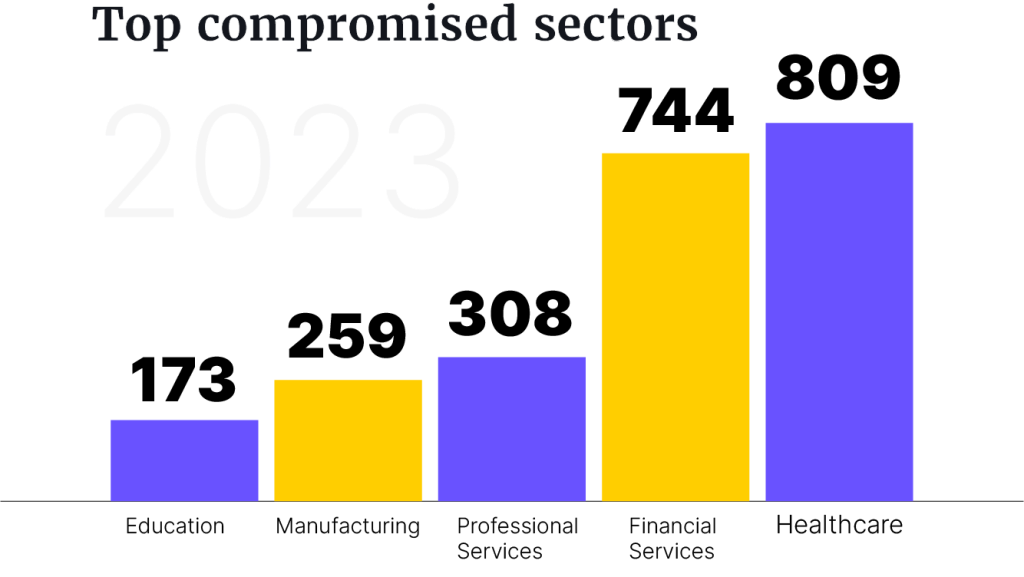
The healthcare sector faced most compromises, 809 in total, followed by the financial services sector with 744 compromises. The healthcare, financial services and transportation sectors reported more than double the compromises compared to 2022. Close to 11% of all publicly traded companies also said they had been compromised in 2023.
Another trend for 2023 was the increase in supply chain attacks (third-party vendor attacks), where 242 breaches/exposures were noted – affecting estimated over 54 million victims. Since 2018, the number of affected organizations has increased by 2,600%.
In total, ITRC identified:
- 3,205 compromises in total – 353,027,892 victims;
- 3,122 data breaches – 349,221,481 victims;
- 25 data exposures – 960,700 victims; and
- 56 unknown compromises – 148,983 victims.
The total attack vectors were:
- Cyberattacks: 2,365 breaches – 343,338,964 victims;
- System and human errors: 729 breaches/exposures – 6,715,385 victims;
- Physical attacks: 53 breaches/exposures – 127,832 victims; and
- Supply chain attacks: 242 breaches/exposures – 54,432,431 victims.
The breach with the most victims in 2023 happened at T-Mobile in January, where 37 million customers’ information was breached. The leaked data included name, billing address, email, phone number, date of birth, T-Mobile account number and information such as the number of lines on the account and plan features.
Still, the estimated number of victims dropped 16% from last year, which is a result of “organized identity criminals focusing on specific information and identity-related fraud and scams rather than mass attacks”, ITRC said.
Regardless of the increasing breaches, the ITRC worries about a large unreported number of breaches. To get a clearer view of the cyber threat landscape, ITRC therefore suggests adopting uniform provision, where any data breach should be filed with state and federal agencies of jurisdiction within 24 hours.
“The two-decade old legislative and regulatory framework designed to alert consumers to breaches is broken,” says Eva Velasquex, CEO Identity Theft Resource Center. “We need to bring a level of uniformity to the breach notice process to help protect both consumers and business.”